Internet is most important service today. Digital information is shared over the internet and we can search what we want to know on a browser and buy something without knowing the background technologies. Do you know how computers work together to identify the computer where you want to send/receive data?
IP address
When a computer needs to communicate with other computer it somehow needs to find the destination. All computers have unique ID called IP address which consists of 32 bits and it is divided into 4 parts like 192.168.0.1 for human readability. A computer can communicate with the target computer by sending data with the unique IP address.
IP address is roughly divided into 2 part, network part and host part. Network part is something like a area and host part is a person who lives there. Each area has its own and each person his own address within the range. Following table shows that network part is 16 bits but it is not always 16 bits in real.
| 1100 0000 0000 0000 | 0000 0010 0110 0100 |
| Network part | Host part |
Global and Private IP addresses
There are two type of IP addresses, global IP address and private IP address.
| Global IP address | It’s unique ID all over the world. This is assigned to a server or rooter which is directly connected to the internet. |
| Private IP address | It doesn’t exist on the internet. This is used to build local network in a company for example. |
Since private IP address must not exist on the internet its range is defined as following.
| Start | End |
| 10.0.0.0 | 10.255.255.255 |
| 172.16.0.0 | 172.31.255.255 |
| 192.168..0.0 | 192.168.255.255 |
Following image shows an example to assign IP addresses within a network. A router connected to the internet has global IP address and private IP address. Other computers in the same network have only private IP address. All computers in the network communicate with a computer on the internet via the global IP address by using NAT (Network Address Translation). Since the internal computer doesn’t have global IP address it’s necessary to change it to global IP address. By sharing the global IP address, all computers under the network can communicate with someone on the internet.
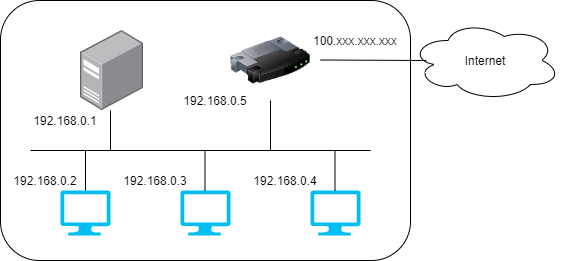
Routing control
In this example above, a router is located as a door to connect internal network and internet but it can also be located between internal networks. When it receives a packet from somewhere it determines where to send it. If the destination is in the own network it sends the data to the own network, otherwise to the other network. Network part is used for this purpose. For example, this router knows that it must send a packet to 192.168.100.0/24 network if the destination is 192.168.100.22.

This routing control is done by unit of block because top level router has to handle a lot of packets, so it is important to reduce it for performance. When we want to open a web site the packet is sent to a router and it determines where to send it. And then, next router will do the same thing. It sounds that all computers have to have IP address list to communicate with someone. It was true at the beginning of the internet but currently not.
Using name instead of IP address
We don’t have to consider about IP address when we want to open a web site. IP address is not so nice when we want to communicate with other people because it’s number. We don’t want to say something like
Open a web site xxx.xxx.xxx.xxx and search YYYYY. You can buy the book there.
It’s much better and easier to say
Go to Amazon.com and search YYYY. You can buy the book there.
As you know, when we open a web site we can see the name like https://www.technicalfeeder.com/ on the address bar. The part www.technicalfeeder.com is called Domain. By means of Domain name, we can easily use the internet without knowing its address. Another advantage to use Domain name is that it can make it abstract.
Imagine that you have your own web service and need to move it to another server in another network because the server provider will no longer be available. It means that the IP address to access to the service will change because different address block is assigned to the provider. If you don’t have your own name you have to tell your new IP address to all users. However, Domain name with DNS server takes care of it and we don’t lose any existing users.
Name resolution
Okay, let’s use name instead of IP address but who knows the name and the IP address? Yes, it’s DNS server. A client software called stub resolver gives a request to a cache DNS server to resolve the name. The cache DNS server gives a request to another DNS server which manages Domains, and the DNS server does the same thing. Following is more precise steps.
- A client asks to cache DNS server to get IP address of Domain name
example.com - Cache DNS server asks a root server
- A root server answers that “DNS server for com” knows
- Cache DNS server asks “DNS server for com”
- “DNS server for com” answers that “DNS server for example.com” knows
- Cache DNS server asks “DNS server for example.com”
- “DNS server for example.com” answers the IP address
- Cache DNS server gives the IP address to the client
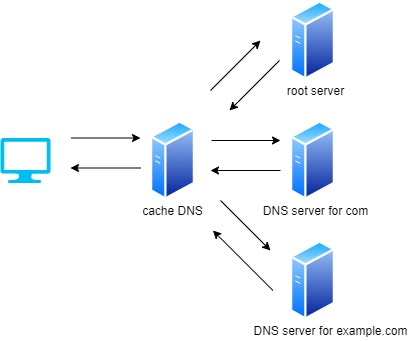
If the root server receives a lot of requests it can’t handle them all in a short time. To reduce the number of requests, client and DNS server has cache. Next time the client wants to resolve the Domain name it can extract the info from the cache. When another computer asks the same Domain name cache server can immediately answer the IP address without asking the root server. However, since DNS is hierarchical structure the data stored in those server can be changed. If its cache data remains forever it doesn’t work correctly in this case. Each server defines timeout period and its server will fetch the info after the time elapsed.
DNS for email
DNS is used not only for seeing web site but also sending email. As you know, an email address contains domain name like username@example.com. It means a sender needs to resolve the domain name and send an email with the IP address. Following process runs in the background.
- A mail client sends an email to a mail server (sender)
- Sender sends a request to a DNS cache server to know a destination mail server (receiver) of the domain (e.g.
mail.example.com) - DNS cache server communicates with other DNS servers and receives IP address of the receiver
- Sender sends an email to the IP address
- A receiver receives the email and put it into a user’s mailbox
This is the process to send an email. If DNS doesn’t work well email can’t be sent correctly. You may receive lots of emails everyday and sometimes see spam mails. DNS is used to detect such emails as well by SPF, DKIM.
SPF stands for Sender Policy Framework. Since a spam mail sender doesn’t want to be identified they use false name for the emails. However, DNS can detect them by checking the domain name of the sender address and IP address of the source.
DKIM stands for Domain Keys Identified Mail. While SPF works in receiver side, DKIM works in both side. It enables receiver to verify that the email is sent by correct server by Public-Key Cryptography. A sender server signs to an email by private key and a receiver verifies the signature by a public key. If a receiver judges that the email is spam mail the mail server puts it into spam mail box or deletes it.
Availability and reliability
Internet is used all over the world. It means that DNS server should work 24 hours. If we want to provide a service which is available 24 hours it’s necessary to chose stable and reliable DNS server to manage our own domain. Normally, when subdomain is created under a domain a DNS server which manages the top level domain delegates the management and operation to subordinate DNS server.
Let’s see a example subdomain.example.com. com is managed by a top level DNS server but example.com is managed by a different server and subdomain.example.com as well. The higher level the DNS server is, the more availability it needs because top level domain has more access than lower level domain does. As I explained above, it’s because cache DNS server asks top level server first.
If DNS server is not well managed its server may be poisoned by DNS cache poisoning. DNS cache server stores data to cache while it communicates with other DNS servers to get destination server’s IP address. The cache is important to reduce number of requests to other DNS servers but DNS cache poisoning can make the server store the fake information. Why does it happen?
DNS uses ID which is 16 bits. This ID is used to know which response is for which request. If the response ID is different from the request ID its message is discarded. If both of them are the same ID cache server stores the info. Since it’s 16 bits its range is small and a computer can create all possible IDs. Cache server sends a request to another server when it receives a request from an attacker. Cache poisoning succeeds if the attacker can send fake info with the same ID while cache server is waiting for the response. UDP protocol is used to communicate for DNS. Its communication cost is lighter than TCP but it is easier to fake the packet and DNS message.
If cache server is poisoned lots of users go to fake web site and may enter user name and password. When you need to chose DNS server the reliability is very important factor to chose.
What you learnt
A computer uses IP address to identify the destination.
IP address is roughly divided into 2 parts, Network part and host part. Network part is used to determine where to send a packet that a router receives.
Since top level router has to handle a lot of packets it is important to reduce the requests for performance. By managing the route control by IP address block, the number of addresses that the router handles can be reduced.
DNS takes care of IP address change and enable us to use name instead of IP address. Even if a server is moved to another place we can find it by DNS. Those steps described above is done completely under the hood and it can make our life easy.
DNS is used for email as well. It can detect spam mail by SPF by checking IP address and domain name. Another way is DKIM which sign to an email by private key and verify it by public key.



Comments